VxWorks 6.9.4 is a specific patch release within the VxWorks 6.9 family, a real-time operating system (RTOS) developed by Wind River Systems (now part of Aptiv). , it focuses on stability, security enhancements, and support for embedded systems in mission-critical environments. This version addresses vulnerabilities in earlier 6.9 sub-releases (e.g., 6.9.4.4) and is commonly used in aerospace, defense, industrial automation, and networking devices.
Key Features and Improvements in 6.9.4
- Core Enhancements:
- Improved IPv4/IPv6 networking stack (IPnet) with better handling of TCP sequence numbers and packet options to mitigate predictability attacks.
- Enhanced kernel configuration via Workbench IDE (version 3.x), supporting GUI and command-line tools like vxprj for reproducible builds.
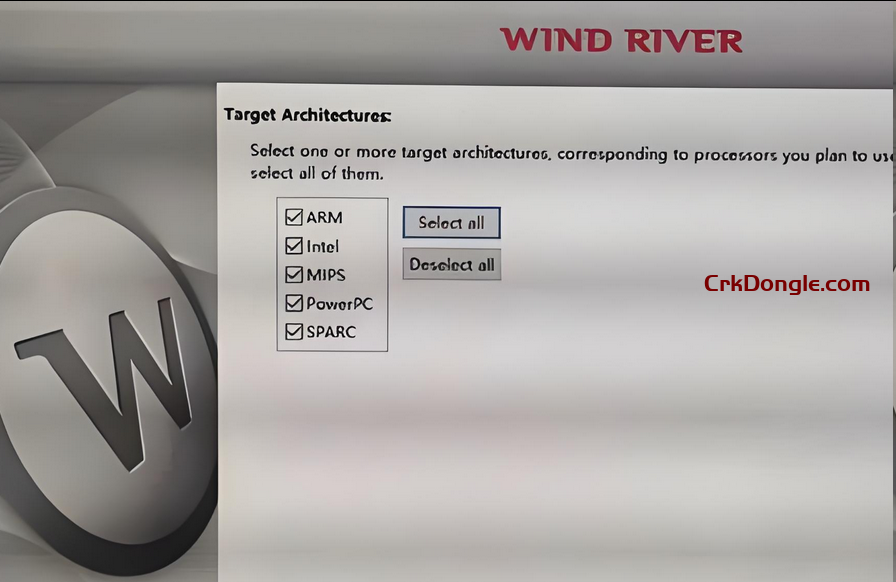
- Support for a wide range of architectures: ARM, PowerPC, x86, SPARC (e.g., LEON processors from Gaisler), MIPS, and more.
- Development Tools:
- Integrated with Wind River Workbench (Eclipse-based IDE) for debugging, profiling, and multi-core support.
- Includes Wind River Diab Compiler 5.9.x and GNU Compiler 4.8 for optimized code generation.
- Board Support Packages (BSPs) for custom hardware, with full source access under license.
- Applications: Widely deployed in legacy systems like routers (e.g., Ericsson SmartEdge), RTUs (e.g., Schneider Electric SAGE), and space hardware (e.g., Gaisler’s LEON SPARC ports).
Security Considerations
VxWorks 6.9.4 includes patches for several high-severity vulnerabilities identified in prior releases, but it’s not immune to all issues. Key CVEs affecting or addressed in 6.9.4:
| CVE ID | Description | CVSS v3 Score | Mitigation Status in 6.9.4 |
|---|---|---|---|
| CVE-2019-12255 | Buffer overflow in TCP/IPv4 component via oversized receive window. | 9.8 (Critical) | Patched; update from pre-6.9.4.4 versions recommended. |
| CVE-2019-12256 | Stack overflow in IPv4 options parsing, leading to potential RCE. | 9.8 (Critical) | Patched in 6.9.4.4 and later; applies to bootrom stack too. |
| CVE-2015-0992 | Predictable TCP ISN generation, enabling session spoofing. | 7.5 (High) | Resolved via patches in 6.9.4.4; verified in devices like SAGE RTU. |
| CVE-2019-12258 | Memory leak in IGMPv3 client. | 5.9 (Medium) | Addressed in 6.9.4 patches. |
| Various (e.g., DHCP buffer overflows) | Heap overflows in DHCP parsing and RPC authentication. | 7.5–9.8 | Patched; affects 6.6–6.9 series, fixed in 6.9.4. |
For full CVE details, refer to NVD or CISA advisories. Wind River recommends upgrading to VxWorks 7 (SR-series) for ongoing support, as 6.9 entered Legacy phase around 2020.
Lifecycle and Support
- Status: Legacy (per Wind River and partners like Gaisler). End-of-general-support was ~2019–2020, but extended maintenance available via contract.
- Upgrades: From earlier 6.9.x (e.g., 6.9.3) or 6.8. Patches downloadable via Workbench maintenance tool with a valid license.
- Documentation:
- VxWorks Application Programmer’s Guide 6.9 (covers APIs, multitasking, and networking).
- Kernel Programmer’s Guide (focuses on configuration and internals).
- Available via Wind River’s portal